The error message “Authorization grant type is not supported by the authentication server” typically occurs when the authentication server does not recognize or support the specific grant type requested during the OAuth or OpenID Connect (OIDC) authentication process.
In my case:
This error through in my laravel.log
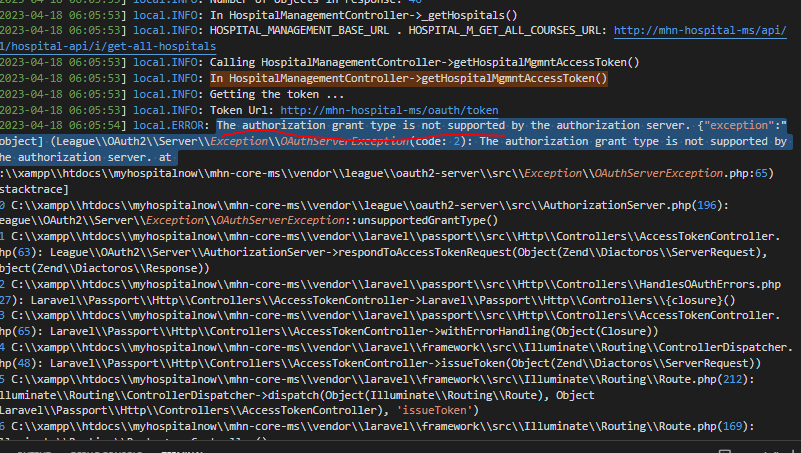
In .env file by mistake I forget to write my QUOTE_M_GRANT_TYPE
AFTER writing this then this problem will resolve
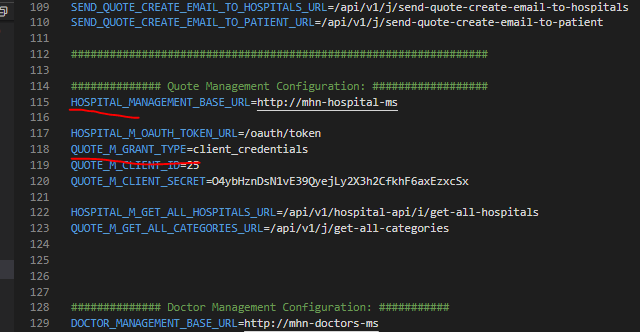
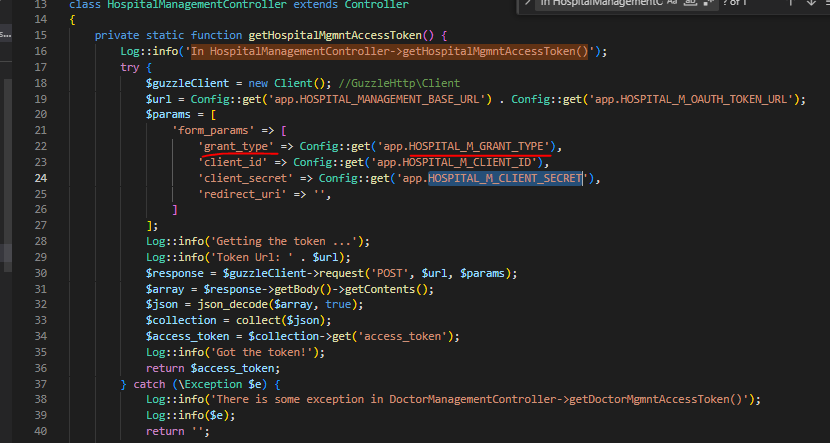
NOW, Here i define in my controller function HOSPITAL_M_GRANT_TYPE
Here are a few possible reasons and steps you can take to troubleshoot this issue:
Verify the supported grant types: Check the documentation or specifications of the authentication server you are using to confirm which grant types are supported. OAuth 2.0 defines several grant types, such as authorization code, implicit, client credentials, and resource owner password credentials. OIDC adds an additional grant type called hybrid. Ensure that you are using a supported grant type according to the server’s capabilities.
Check the request parameters: Review the request parameters you are sending to the authentication server. Verify that you are including the correct grant type parameter (grant_type) and its value. Make sure it matches one of the supported grant types of the authentication server.
Validate the client credentials: Ensure that you are providing the correct client credentials (client ID and client secret) when making the authentication request. The authentication server may reject the request if the client credentials are invalid or not properly configured.
Verify the endpoint URLs: Double-check the endpoint URLs you are using for authentication. Ensure that the authorization endpoint and token endpoint URLs are correct and correspond to the authentication server’s configuration.